Ball Bearing Insert Ref. Ina Gehme07-gg-n - g g bearing
Your system must have enough storage capacity to accommodate the size of your target artifact. For images, your system must have sufficient space for its uncompressed size.
When switching to a different region, ensure that the TMAS_API_KEY, which is stored as an environment variable, is associated with that Trend Cloud One region. A mismatch causes the scan command to fail with a 403 Forbidden or APIKeyPlatformMismatchError error.
Crossed roller bearingapplications
Use the preceding flag to override false positives or other vulnerability findings you want to ignore. For more information, see Override vulnerability findings.
This flag allows you to specify which platform or architecture to use when scanning multiple-architecture container images:
Trend Micro Artifact Scanner (TMAS) performs pre-runtime vulnerability and malware scans on artifacts (see Supported artifacts), enabling you to identify and fix issues before they reach a production environment such as, for example, Kubernetes for container images.
Thk crossroller bearing

For example, Jenkins projects can automatically build, test, and push Docker images to a Docker registry. Once pushed, the image may be instantly available to run in an orchestration environment. If open source vulnerabilities exist in the image, then they are a risk when the image is run. Since images are intended to be immutable, images should be scanned before they are deployed to a cluster.
Note that the TMAS CLI can also be used in Trend Vision One with enhanced capabilities, such as secret scanning. For more information, see About Trend Micro Artifact Scanner in Trend Vision One.

To ensure optimal performance and access to the latest features, upgrade to the most recent version of TMAS on a regular basis, as follows:
If TMAS reports a vulnerability which has been determined to be a false positive or any other finding you wish to ignore, you may instruct TMAS to override these findings by defining one or more rules in an override configuration file (for example, ~/tmas_overrides.yml). Overriding malware findings is not supported at this time.
The vulnerability overrides are structured as a list of rules. Each rule can specify any combination of the following criteria:
A given vulnerability finding is overridden if any of the rules specified in the override file apply to the finding. A rule is considered to apply to a finding only if all the fields in the rule match those found in the vulnerability finding:
Crossed roller bearingvs ballbearing
TMAS scans artifacts inside your CI/CD pipelines. You can install the TMAS CLI into your CI/CD pipeline to perform scans before artifacts are deployed to production. In the case of vulnerability scans, TMAS takes the artifact that you wish to be scanned and generates a Software Bill of Materials (SBOM). It then uploads the SBOM to Trend Cloud One for processing and returns a vulnerability report.
Hiwin crossroller bearing
When the --saveSBOM flag is enabled, the generated SBOM is saved in the local directory before it is sent to Trend Cloud One for scanning.
JRA series crossed roller bearing is designed with integral inner ring and split outer ring to reduce the thickness of inner and outer ring to the minimum of 16mm. The ultrathin crossed roller bearing includes three product models which have same dimensions while different types of outer rings: JRA series crossed roller bearing is designed with horizontally split outer ring, JRA-C series crossed roller bearing with vertically split outer ring and JRBS series crossed roller bearing with integral outer ring. These compact crossed roller bearings are suitable for applications where limited space and light weight are required, such as rotating parts in industrial manipulators and robots.
LYJW is a professional manufacturer of slewing bearings and we can design and manufacture slew ring bearings, precision bearings, slew drives and custom bearings for construction, engineering, mining, marine, chemical, military, wind turbine, medical equipment, and many other industries. By virtue of expertise team, advanced manufacturing technologies and strict quality management system, LYJW takes the lead in the R&D of slewing bearings, which are designed with reasonable construction, light weight, good load carrying capacity and high versatility. The bearingsâ diameters range from 200 to 15000mm and the accuracy covers PO, P6 and P5 class. Now, we can manufacture CCS, ABS, BV, GL and other certified bearings. We adhere to the business principle of âQuality and Integrityâ and weâll keep providing outstanding bearings and superior services to serve global customer.
Adjust your system's binary path settings by replacing the existing TMAS binary with the updated TMAS binary. For information, see the Add TMAS CLI to your PATH step described in Set up.
Memory consumption of the TMAS CLI scales with the number of files an artifact contains. Some artifacts may require additional memory to complete successfully. Performance can be improved by increasing memory resources and CPU cores.
Linearcrossed rollerbearings
Crossed roller bearingSKF
This flag is necessary when attempting to scan images from the Docker or Podman daemon with different architectures than the host that is running TMAS.
Each scan initiated against a registry image using the Trend Micro Artifact Scanner generates a new temporary directory under $TMPDIR to download and analyze the image.
Schaeffler crossroller bearing
Any vulnerability finding that matches a rule is presented in the JSON report in an "Overridden" section, rather than classified under its severity:
For more information on available scanners and their flags, see Scan subcommands. Using a scanner-specific flag without enabling the associated scanner does not result in an error, but that flag does have no effect.
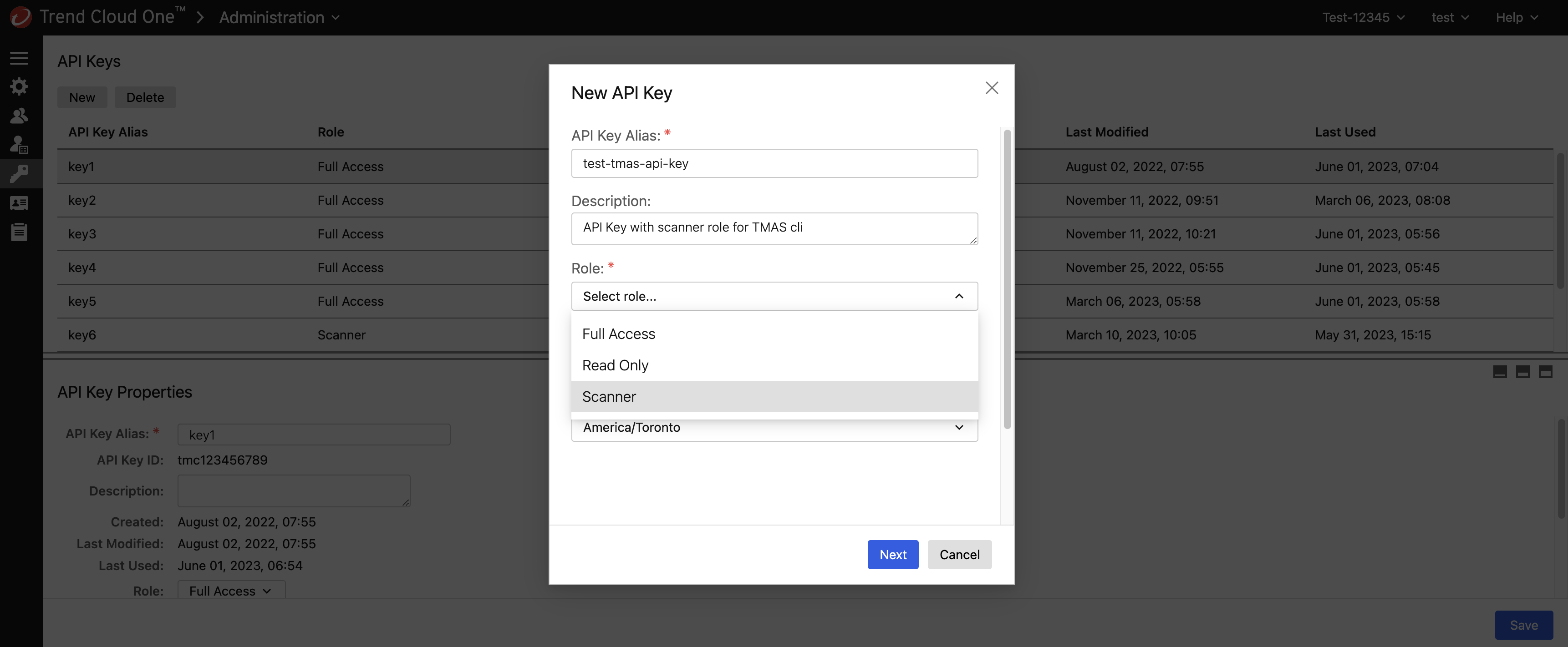
The TMAS CLI requires a valid API key to be stored in the environment variable. Add the API key associated with the Trend Cloud One region that you wish to call as an environment variable TMAS_API_KEY, as follows:
Established in 1998, Luoyang Jiawei Bearing Manufacturing Co., Ltd. (LYJW) is a professional manufacturer of slewing bearings and we can design and manufacture single-row ball slewing ring bearing, double-row ball slewing ring bearing, three-row roller slewing bearing, ball-roller combination slewing ring, crossed roller bearing, crossed tapered roller bearing, slew drives and custom bearings.
Using a registry as an artifact source does not require a container runtime. In addition, scan results from registry artifact sources can be used for policy evaluations in Trend Cloud One Container Security.
face-mount crossed-rollerbearing
For version 1.35.0 and later, this tool automatically removes those temporary files after scan execution. To clean up existing temporary files that were generated with prior versions or by an interrupted scan, use the following commands (or its platform equivalent) under your discretion:
When obtaining the API key, ensure that the API key is associated with the endpoint you are calling. For instance, create an API key in a us-1 account if you are planning to call the us-1 region endpoint to ensure proper authorization.
Each rule must also be accompanied by a reason indicating why the rule was implemented. For example, false positive, mitigated, vulnerable package function is not called, and so on:
Attempting to specify an architecture for multi-arch registry images without support for that architecture results in an error.
Scanning images from private registries requires that you login to the registry using tools such as docker login before attempting the scan. TMAS follows Docker's authentication behavior in order to use Docker's pre-configured credentials. When running malware scans on images from private registries and using Docker credsStore (.docker/config.json), add the credential-helpers= configuration in the .config/containers/registries.conf file. For example, if Docker credsStore is desktop, add credential-helpers = ["desktop"]. When running malware scans on images from private registries on Docker Hub, ensure that you log in with the server name https://docker.io or docker.io. For example, docker login docker.io.




 8613869596835
8613869596835