Full ceramic vs hybrid bearing - hybrid bearings
Alemite LTD GREASE GUN | Develops up to 10000 psi pressure, Rugged and light weight die cast aluminum head, Vinyl cover for a comfortable and sure grip, ...
Detroit Axle is a leading global retailer and distributor of OE re-manufactured and new aftermarket auto parts. We are committed to providing first-class products and outstanding customer service at an incredible value.
202114 — INTRODUCTION A cam is a mechanical device used to transmit motion to a follower by.
2006Chevy Cobalt Wheel Bearingreplacement
Another way of making decisions for Automatable is to identify barriers posed by the device that make it difficult for attackers to exploit vulnerabilities. Vulnerability Chaining and open connectivity to the internet can enable attackers to exploit a vulnerability by using other weaknesses. To decide on a value of No or Yes, analyzer algorithms must consider all reasonable scenarios.
2007Chevy Cobaltfrontwheel Bearingreplacement
This determines what is the impact on the Mission Essential Functions of Relevant Entities. A mission essential function (MEF) is a function directly related to accomplishing the organization’s mission as set forth in its statutory or executive charter. Identifying MEFs is part of business continuity planning or crisis planning. In contrast to non-essential functions, an organization “must perform a [MEF] during a disruption to normal operations.” The mission is the reason an organization exists, and MEFs are how that mission is realized.
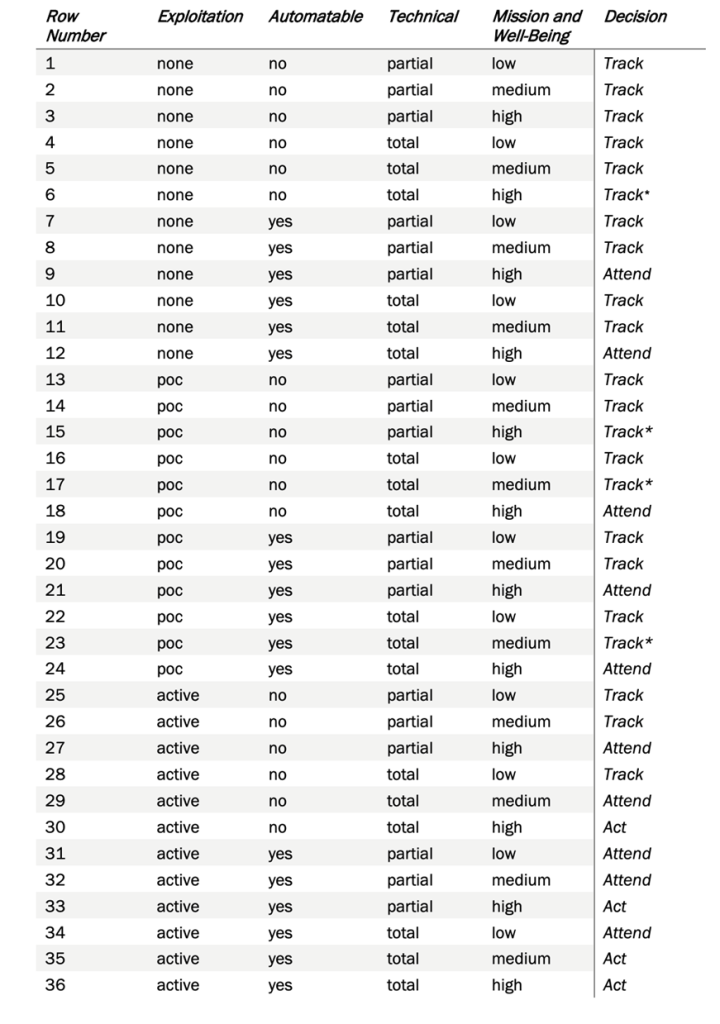
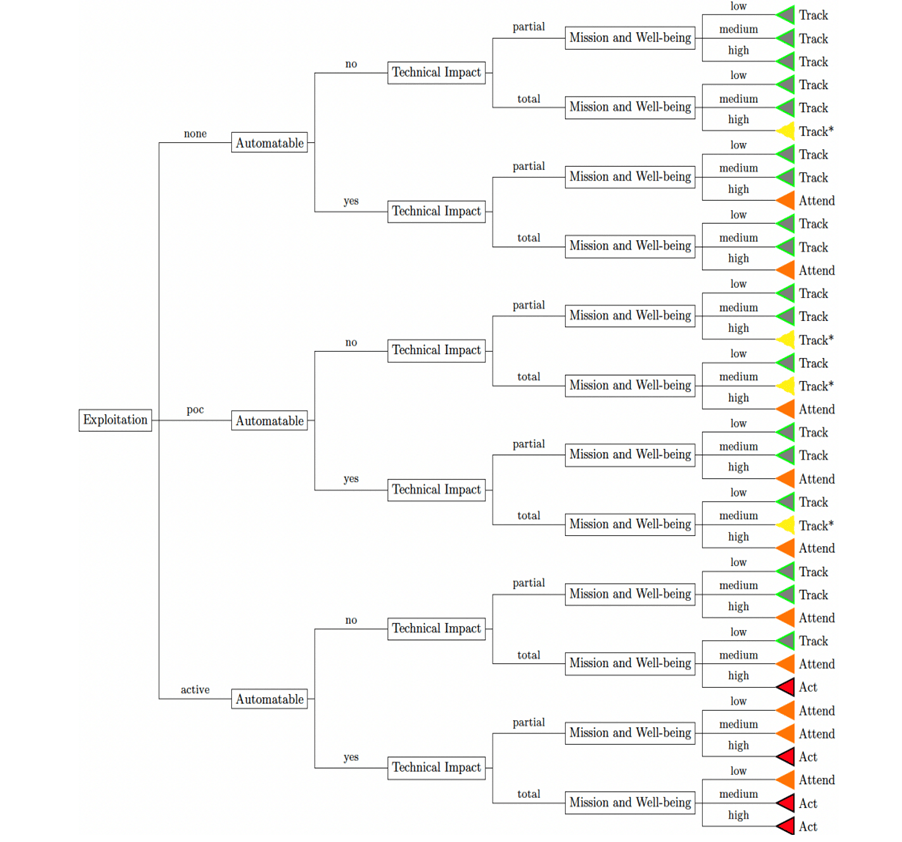
Stitching all the decision factors together gives a Decision Tree of CISA SSVC. It meticulously determines a vulnerability to be considered either as Act, Attend, Track*, or Track on a specific device. The same vulnerability on another device may fall into a different category (Act, Attend, Track* or Track) based on the characteristics analyzed while deriving the four decision points – Exploitation, Technical Impact, Automatable, and Mission Prevalence. Defying the fact that prioritization based on the severity score of a vulnerability would have resulted in vulnerabilities of two devices being considered as same priority, CISA’s Stakeholder Vulnerabilities Categorization provides a unique approach to the risk prioritization algorithms.
2010 Chevy Cobalt wheel bearingreplacement
Any evidence of active exploitation of a vulnerability through various sources such as CISA Known Exploited Vulnerabilities (KEVs), other certified information from various internet sources, National Vulnerability Database (NVD) plays an important role in decision-making.
HOUSE BILL 2936. By Faison. HB2936. 013057. - 1 -. AN ACT to amend Tennessee Code Annotated, Title 33;. Title 36; Title 37; Title 49; Title 63 and Title 68 ...
There are four factors that determine a vulnerability on a device to be one Act, Attend, Track*, Track. The decision-making points embrace reasonable assumptions made with a prior understanding of a vulnerability and scenarios. The four factors comprise Exploitation, Automatable, Technical Impact, and Mission Prevalence.
If a vulnerability discloses authentication or authorization credentials to the system, this type of information disclosure should also be scored as Total if those credentials give an adversary total control of the component. This implies that Technical impact has a scope and is relative to the affected component where the vulnerability resides.
It represents the ease and speed with which attackers can exploit the vulnerabilities. We can mark Automatable as Yes if we can reliably automate steps 1-4 of the Kill Chain. Developed by Lockheed Martin, the Cyber Kill Chain® framework is part of the Intelligence Driven Defense® model for the identification and prevention of cyber intrusion activity. The model identifies what the adversaries must complete in order to achieve their objective.
202327 — The average cost for a Chevrolet Silverado 2500 HD wheel bearing replacement is between $384 and $489. Labor costs are estimated between $179 and $226 while ...
We, at SecPod, discovered a thought-provoking document from CISA on Stakeholder Specific Vulnerability Categorization (SSVC), a customized decision tree model that assists in prioritizing vulnerability response for customers by evaluating vulnerabilities. The goal of SSVC is to assist in prioritizing remediation based on the impact a vulnerability exploitation would have on the organization(s). The decision tree determines four possible outcomes for a risk – Track, Track*, Attend, and Act. The table below explains Vulnerability Decisions and Possible Outcomes.
high quantities 608RS Bearing 608RS dimension: 8x22x7, Enquiry for global 608RS Deep Groove Ball Bearings suppliers Old model:608RS, Cr:3.38 kN, ...
Wheel Bearing and Hub Assembly (Rear). Volkswagen Jetta. Genuine Volkswagen Part - 1T0501611AJ (1T0-501-611-AJ). Ships from Franklin Wisconsin.
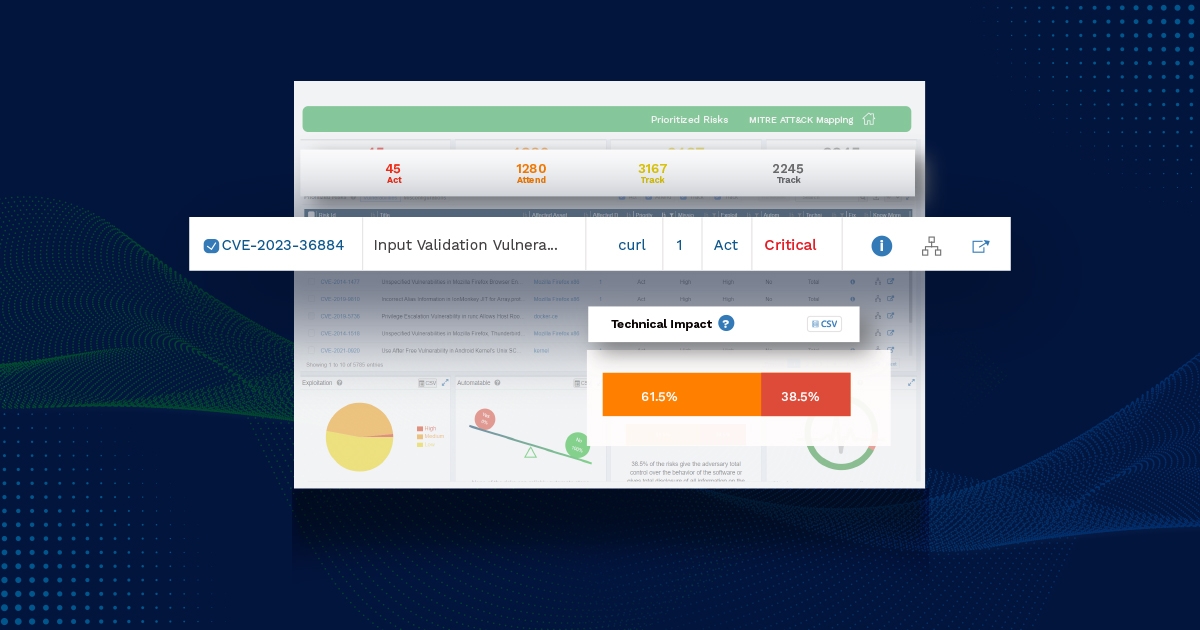
Risk Prioritization is not a new technology in the cyber security space. Cybersecurity professionals look for products that can integrate with existing vulnerability assessment reports to help prioritize risks, most often just software vulnerabilities. Primitive modus operandi such as Prioritization based on the Common Vulnerability Scoring System (CVSS) is an easy go-to approach for ordering mitigation plans. Should we also consider a step forward? What also matters is the stakeholders on which a vulnerability exists. Is the vulnerability on a mission-critical device Is there a mitigation or workaround already in place to avoid vulnerability attacks We not only base our decisions merely on software vulnerabilities but also look deep into the misconfiguration in the systems.
Product Feedback - Let us know what you think about our LJ1095L1-C product. Click here to leave us your feedback. ... Prefer to Request a Quote? ... Click for a new ...
#66045 Not for V-Rod's, will not fit '11-'13 CVO Softail or CVO Dyna. #66047 49-state emissions compliant; earlier models not supported due to many firmware ...
What do you want to do? Select an option; Find information on IEEE 802.11™ · Access the National Electrical Safety Code® (NESC®) · Find MAC, OUI, and Ethernet ...
Front Wheel Hub Assembly - Compatible with 2007 - 2018 Nissan Altima 2008 2009 2010 2011 ... ECCPP Wheel Hub and Bearing Assembly front 515066 fit 2004-2008 ...




 8613869596835
8613869596835