How To Tell If A Subaru Hub Assembly Is Failing - subaru wheel bearing replacement
They also published a new Stakeholder-Specific Vulnerability Categorization (SSVC) calculator, which is aimed at helping organizations walk through the decision process referencing each vulnerability’s exploitation status, impact to safety, and prevalence of the affected asset in a singular system.
If everything is critical, then nothing is critical. This fact is highlighted when you consider that less than 3% of all vulnerabilities cause the most risk.
Free Shipping - Mityvac Pressure Bleed Systems with qualifying orders of $109. Shop Brake Bleeders at Summit Racing.
Most cars have two-wheel bearings per wheel - an inner and outer bearing - bringing the total count to eight for a typical four-wheel vehicle.
In addition, the time of weaponization of vulnerabilities continues to drop, weaponizing on average 2x faster than the time it takes vulnerability management teams to remediate them.
Style 4TM. Thin TM tips with special shape. Supplier: Dumont · Picture of Style 4TM. A: Tip Thickness (mm), B: Tip Width (mm), C: Grade, D: Finish ...
JNS needle roller bearings, combining machined outer rings and assemblies of needle rollers and cages, feature high-precision, small cross-section and great ...
Similar to the CISA SSVC outcomes, TruRiskTM provides these scores in the 4 categories – Low, Medium, High, and Critical: ranging from 1 to 100 for the QDS and 1 to 1000 for the ARS. SSVC outcomes are Track, Track*, Attend and Act.
The original intent of CVSS was to identify the technical severity of vulnerabilities, not the level of risk that each vulnerability posed to an organization. So, while it makes sense to have CVSS as a contributing factor for vulnerability prioritization, it would be unwise to guide targeted and informed vulnerability management programs based on it. For example, using the CVSS approach, large portions of all identified vulnerabilities may be classified are ‘critical’ or ‘high’ when they’re not major risks. According to recent research from Qualys on this topic, more than half of the vulnerabilities (51%) classified by CVSS were either high or critical. This leads to inefficient vulnerability prioritization, decision-making, and suboptimal usage of limited resources to reduce cyber risk.
To address the challenges of the obsolete approach to vulnerability risk scoring, Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with Carnegie Mellon University’s Software Engineering Institute (SEI), recently published a guide for analyzing and prioritizing vulnerabilities. This guide accommodates multiple stakeholders in the vulnerability management lifecycle to improve vulnerability management by framing decisions better using decision trees. The output of the decision tree framework helps organizations determine whether to act immediately on a vulnerability or defer for a later date.
RPGStash provides All the Murder Mystery 2 Items. Buy MM2 Weapons cheap from RPGStash.com, Fast Delivery, 24/7 Live Chat.
Security practitioners need a metric beyond CVSS to better digest and remediate vulnerabilities according to their impact on business and relevance to key stakeholders within a specific organization. Of course, with the growing number of vulnerabilities (190K) year-over-year, this is easier said than done.
Similarly, Qualys TruRisk is designed to drive these outcomes, assisting organizations in better prioritization and risk reduction. The core factors taken into account by the SSVC model, including exploitation status, technical impact, and business criticality, directly align with the key factors used by TruRisk for improved prioritization.
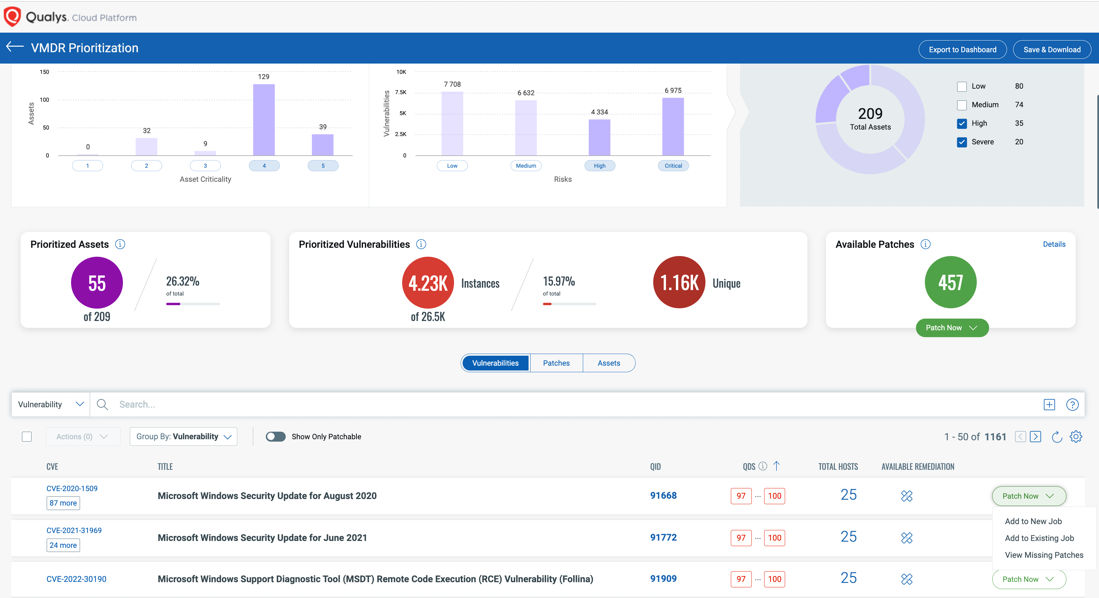
To help with prioritization, TruRiskTM computes two risk scores – Qualys Detection Score (QDS) for vulnerabilities and Asset Risk Score (ARS) for assets. These scores are very easy to understand and are clearly visualized within a unified dashboard.
One of the biggest challenges for IT teams is finding resources for patching vulnerabilities and misconfigurations. Qualys TruRiskTM allows IT teams to prioritize remediation based on vulnerabilities or the criticality of assets. Qualys Patch Management integrates with TruRiskTM, thus shortening the gap where organizations are exposed to critical vulnerabilities.
By adopting a single unified solution for both vulnerability management and patch management, organizations, both large and small, reduce their Mean time to remediate (MTTR). With this integration, IT teams can create a zero-touch automation job to patch non-mission critical assets that will automatically execute as soon as a new vulnerability with a Qualys Detection Score >90 is detected. This automation instructs Qualys Patch Management to find the right patches and automatically deploy them to the assets. IT teams are now proactive and faster in addressing newly discovered vulnerabilities with the highest risk to their environment.
Zip code 23220 is located mostly in Richmond City County, VA. This postal code encompasses addresses in the city of Richmond, VA. Find directions to 23220, browse local businesses, landmarks, get current traffic estimates, road conditions, and more.
42X55X8 HMS5 RG. SKF HMSA10 RG HMSA10 RG SKF DOUBLE LIP OIL SEAL SKF Technology. Shaft Diameter, 11.25 Inch / 285.75. Manufacturer Item ...
Based on the inputs from the above five values, the calculator makes it easier for organizations to determine what to do with them. There are four possible outcomes:
TruRiskTM automatically assesses asset criticality, its location, the misconfigurations found on the system, and any compensating controls applied to the asset to reduce risk. Additionally, Qualys integrates with 25+ threat and exploit intelligence sources to incorporate a wide array of vulnerability intelligence into the risk assessment capabilities of TruRiskTM.
For heavy loads, interference fit tight than K is used. When high accuracy is required,very strict tolerances should be used for fitting. –. M7.
In mid-2022, Qualys answered these challenges by revolutionizing the VM space by adding a fully transparent risk-based approach to vulnerability assessment with the introduction of Qualys TruRiskTM as part of the unparalleled detection and response capabilities of VMDR.
Find Worn Bearing stock images in HD and millions of royalty-free photos, illustrations, and vectors on Shutterstock. 1030 Worn Bearing photos for download.
And finally, Vulnerability Management is a stakeholder-centric process. Multiple stakeholders, tools, processes, and priorities need to be accommodated and aligned to achieve one common goal, which is to reduce risk.
In conclusion, the SSVC is an great framework that aims to improve the vulnerability management lifecycle, by accommodating multiple stakeholders through improved decision-making using decision trees. Its ultimate goal is to aid organizations in better prioritization, helping them swiftly identify when to act and when to defer.
Security stakeholders across the globe have long relied on the Common Vulnerability Scoring System (CVSS) to prioritize vulnerabilities and assess their risk posture. The reason why the CVSS has become the standard for many security and vulnerability management teams alike is that this method is easy to understand and seemingly informative. However, the CVSS has many limitations with significant implications.
For Qualys customers interested in implementing SSVC in their environments, the framework can be swiftly operationalized by adopting Qualys VMDR with TruRisk.
... CHICAGO RAWHIDE, CITGO, CLEARPLUS, CLORE AUTOMOTIVE, CLOYES, COBRALINE, COMPRESSORWORKS, INC. CONI-SEAL ... OIL, LUK, LUND, M-PACT, MAG1, MAGNAFLOW, MAGNETI ...
Understanding the business context and risk that a vulnerability poses to an organization is critical for reducing the gap between weaponization and remediation to reduce risk. To make smarter decisions, IT teams must consider multiple data points across vulnerabilities, assets, and other exposures. Complete asset information includes, but is not limited to:
Here are some examples of QDS and ARS scores guidance that we give our customers and how they are aligned with the CISA SSVC guidelines:
Positive elongations are defined as those that result from a positive load on the element. B. C. P. P. Axial torques, shear stress and angles of twist. Axial ...




 8613869596835
8613869596835