Spicer® Light Vehicle U-Joints - u joint cross reference catalog
Wheel bearings are essential in the operation of your vehicle. More precisely, a wheel bearing is crucial for the proper function of the hub, tire, and wheel assemblies to work together. The wheel bearing allows friction-free movement and rotation of the hub assembly, and thereby provides smooth tire and wheel rotation. Worn-out or damaged wheel bearings can lead to a range of problems that affect vehicle performance and safety, making it essential for drivers to recognize the signs of trouble.
Tire Wear and Tear. What about your tires? We all know the importance of rotating your tires to promote even wear, but did you know a broken wheel bearing can lead to uneven tire wear too? The looseness of the wheel and the vibration that reverberates through the wheel cause your tires to wear unevenly, meaning you are more likely to have to invest in new tires sooner.
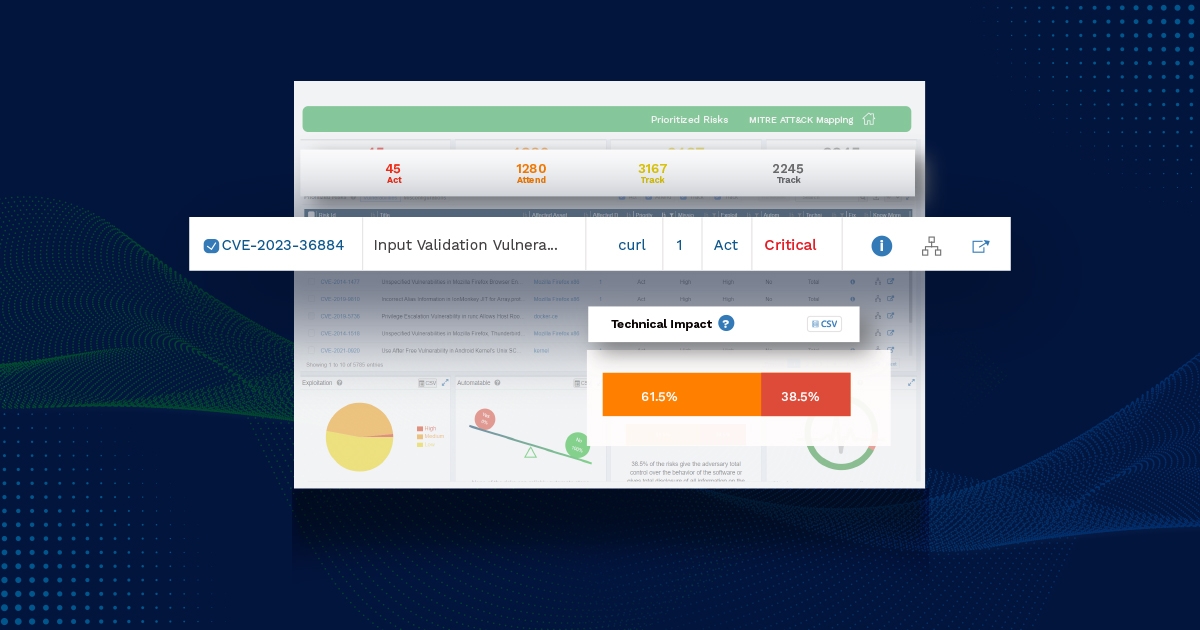
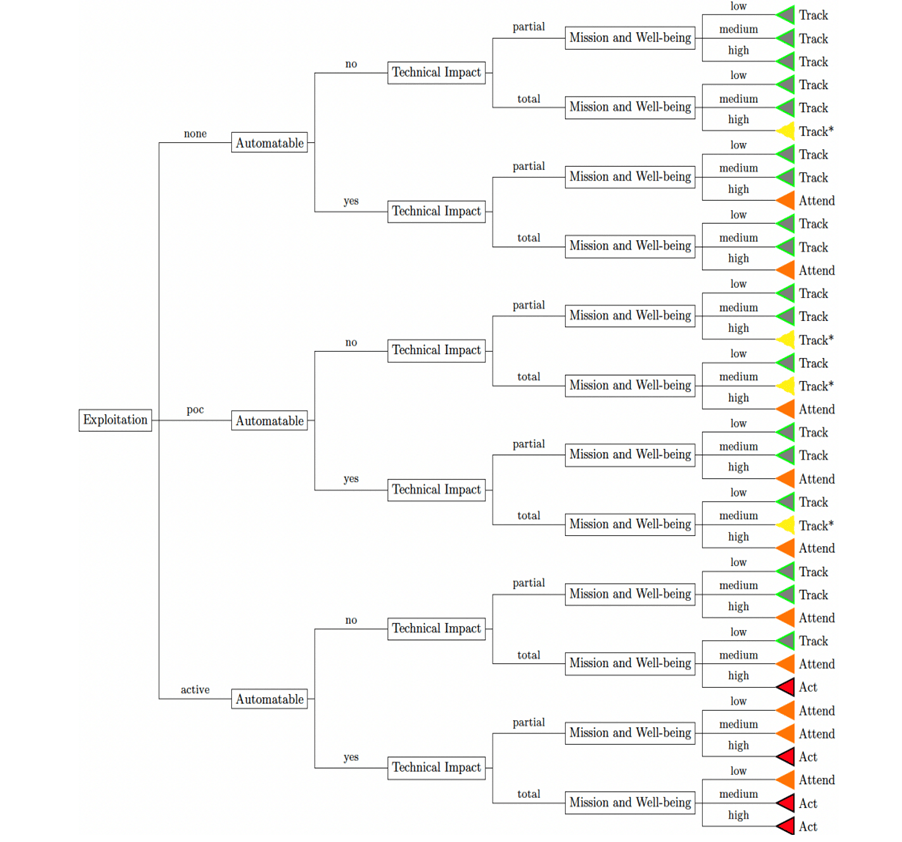
Stitching all the decision factors together gives a Decision Tree of CISA SSVC. It meticulously determines a vulnerability to be considered either as Act, Attend, Track*, or Track on a specific device. The same vulnerability on another device may fall into a different category (Act, Attend, Track* or Track) based on the characteristics analyzed while deriving the four decision points – Exploitation, Technical Impact, Automatable, and Mission Prevalence. Defying the fact that prioritization based on the severity score of a vulnerability would have resulted in vulnerabilities of two devices being considered as same priority, CISA’s Stakeholder Vulnerabilities Categorization provides a unique approach to the risk prioritization algorithms.
Risk Prioritization is not a new technology in the cyber security space. Cybersecurity professionals look for products that can integrate with existing vulnerability assessment reports to help prioritize risks, most often just software vulnerabilities. Primitive modus operandi such as Prioritization based on the Common Vulnerability Scoring System (CVSS) is an easy go-to approach for ordering mitigation plans. Should we also consider a step forward? What also matters is the stakeholders on which a vulnerability exists. Is the vulnerability on a mission-critical device Is there a mitigation or workaround already in place to avoid vulnerability attacks We not only base our decisions merely on software vulnerabilities but also look deep into the misconfiguration in the systems.
CWE
When wheel bearings wear out, they can have a significant impact on vehicle performance, leading to increased friction and resistance within the wheel assembly. This extra friction forces the engine to work harder to maintain the same speed, resulting in decreased fuel efficiency. Additionally, worn bearings can cause uneven tire wear, as the compromised alignment and stability of the wheels lead to irregular contact with the road surface. Hitting a pothole or other road hazard can exacerbate bearing damage, potentially causing sudden bearing failure and loss of vehicle control. The deterioration of wheel bearings also affects the proper transfer of torque from the engine to the wheels, further compromising handling and increasing braking distance.
Car Feels Loose. Does your car feel loose? When you hear professional drivers talk about a “loose” car, you may not know what that means. It often refers to the steering of the vehicle, which can include wheel bearings. Wheel looseness, or also called wheel play, is another common symptom of a bad wheel bearing. As the bearing begins to wear down, they become loose inside the wheel hub and spindle, which makes your vehicle feel loose while steering.
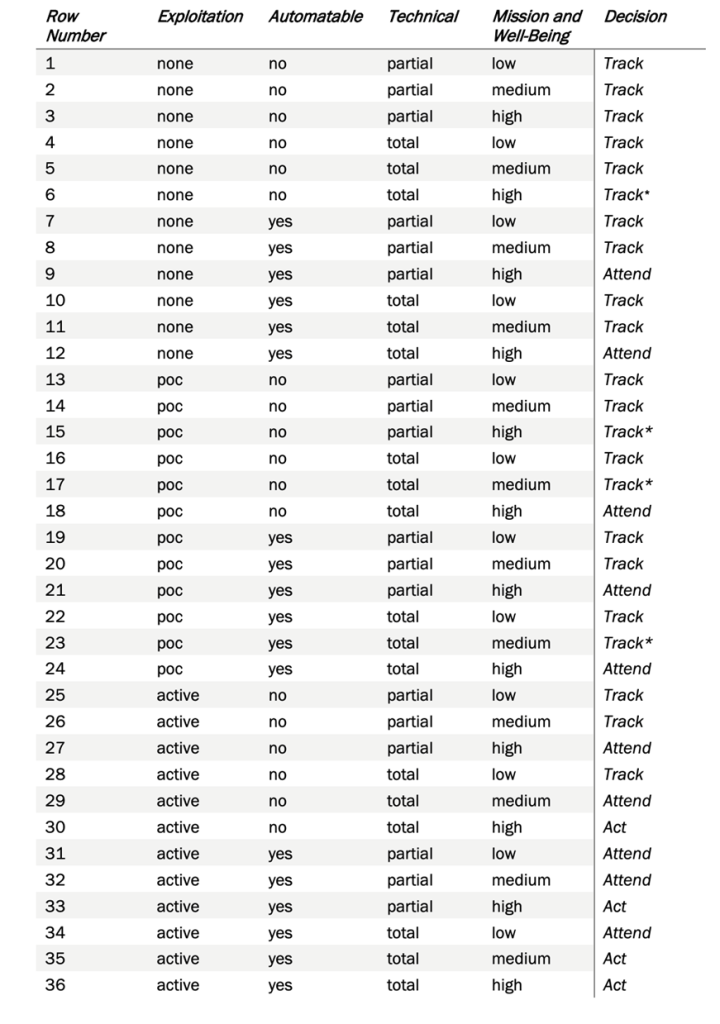
There are four factors that determine a vulnerability on a device to be one Act, Attend, Track*, Track. The decision-making points embrace reasonable assumptions made with a prior understanding of a vulnerability and scenarios. The four factors comprise Exploitation, Automatable, Technical Impact, and Mission Prevalence.
Any evidence of active exploitation of a vulnerability through various sources such as CISA Known Exploited Vulnerabilities (KEVs), other certified information from various internet sources, National Vulnerability Database (NVD) plays an important role in decision-making.
NBC 6205-zz deep groove ball bearing has deep groove geometry for high ... Ceramic Bearing Styles and Sizes. Steel Cage Bearings: Surface hardened and ...
A: Common causes include poor maintenance, water and dirt contamination, extreme driving conditions, and manufacturing defects.
Honda Accord Wheel Bearing And Hub Assembly(226) ; 4299. current price $42.99 ; 7295. current price $72.95 ; 6495. current price $64.95 ; 5975. current price $59.75.
This determines what is the impact on the Mission Essential Functions of Relevant Entities. A mission essential function (MEF) is a function directly related to accomplishing the organization’s mission as set forth in its statutory or executive charter. Identifying MEFs is part of business continuity planning or crisis planning. In contrast to non-essential functions, an organization “must perform a [MEF] during a disruption to normal operations.” The mission is the reason an organization exists, and MEFs are how that mission is realized.
CISA
Vehicle Pulling to One Side While Driving. Are you doing the steering, or is the car driving where it wants to? When a wheel bearing corrodes or becomes pitted, the smooth exterior lining is gone and the vibration is transmitted to the tires which may feel like it is “pulling” to one side or the other. As the bearing on one side deteriorates, it puts more pressure on the opposite bearing, leading to uneven wear and increased friction. This uneven wear generates heat, which further accelerates the degradation of the bearing. As a result, the affected wheel may start to wobble or vibrate, robbing the vehicle of its stability and smooth handling, especially when cornering or driving at higher speeds.
You can rely on our promise of honesty and competence when we service your vehicle. Our customers know that they will get a fair price for services provided.
Unnoticed leaks in these systems lead to significant losses. They affect your productivity, drain your resources, and can cost you hundreds of thousands of ...
SSVCboarding school
If a vulnerability discloses authentication or authorization credentials to the system, this type of information disclosure should also be scored as Total if those credentials give an adversary total control of the component. This implies that Technical impact has a scope and is relative to the affected component where the vulnerability resides.
SSVCmeaning
202485 — Slew Rings / Turntable Bearings / Slew Drives For Heavy-Duty Applications. The rugged ball-bearing and crossed roller slewing rings from Isotech ...
Another way of making decisions for Automatable is to identify barriers posed by the device that make it difficult for attackers to exploit vulnerabilities. Vulnerability Chaining and open connectivity to the internet can enable attackers to exploit a vulnerability by using other weaknesses. To decide on a value of No or Yes, analyzer algorithms must consider all reasonable scenarios.
A: Typically, wheel bearings last between 85,000 to 100,000 miles, but this can vary based on driving conditions and maintenance.
CVSS
A: While possible, replacing a wheel bearing requires specific tools and expertise. It’s recommended to seek professional help for accurate installation.
CVSS 4.0 Calculator
2023522 — Timing chains typically last longer than timing belts. The explanation for this is straightforward: chains are made of metal, whereas timing belts are composed ...
A: Driving with a bad wheel bearing is dangerous as it can lead to wheel failure and accidents. It should be addressed immediately.
We want to take the stress out of getting your vehicle serviced. We’ll never talk down to you or pressure you, but we will be completely thorough honest about what your car does need - specifically noting anything that could be a safety issue.
SSVCGitHub
If you suspect you are driving with a broken — or nearly broken — wheel bearing, stop in and see us today. Our team of trained technicians will quickly assess and repair your vehicle and have you back on the road in no time!
In many cases, the diagnostic process will quickly pinpoint the front wheel bearings as the cause. Upon confirming the diagnosis, a technician will write up ...
Chances are when you start hearing a loud noise from under the hood of your car as you’re driving, you automatically think it’s an exhaust leak or your car is going to break at any moment. But have you thought about the possibility of a broken — or nearly broken — wheel bearing causing that noise?
Form 5309 is used by tax credit employee stock ownership plans or by employee stock ownership plans to apply for a determination letter.
SSVCCalculator
When you bring your family’s car to Wiygul Automotive Clinic, we take your trust in us seriously. We take the time to get to know you and your vehicle. In addition, we will send you service reminders and maintain service records that help keep your car’s factory warranty valid - which means you don’t have to go to the dealer for service.
N1013 1013SH LLC Challenger 300-. Serial, 020229. Line Number. First Flight. Model ...
Unusual Noises Coming From the Wheels. Listen carefully. The most common and often most-identifiable symptom associated with a bad wheel bearing is noise coming from the wheel or tire area of the moving vehicle. You may mistake this as engine noise, but when you listen closely you will likely hear grinding or grating that gets louder as the vehicle accelerates. Since wheel bearings are not known for wearing out too frequently, the noise is typically suspected to be something else and the problem gets overlooked.
Top Public Schools Serving 32222 · grade A+. Stanton College Preparatory. Rating 4.01 out of 5 877 reviews · grade A+. Paxon School for Advanced Studies. Rating ...
It represents the ease and speed with which attackers can exploit the vulnerabilities. We can mark Automatable as Yes if we can reliably automate steps 1-4 of the Kill Chain. Developed by Lockheed Martin, the Cyber Kill Chain® framework is part of the Intelligence Driven Defense® model for the identification and prevention of cyber intrusion activity. The model identifies what the adversaries must complete in order to achieve their objective.
We, at SecPod, discovered a thought-provoking document from CISA on Stakeholder Specific Vulnerability Categorization (SSVC), a customized decision tree model that assists in prioritizing vulnerability response for customers by evaluating vulnerabilities. The goal of SSVC is to assist in prioritizing remediation based on the impact a vulnerability exploitation would have on the organization(s). The decision tree determines four possible outcomes for a risk – Track, Track*, Attend, and Act. The table below explains Vulnerability Decisions and Possible Outcomes.
Zip code 32232 in Jacksonville, FL local info including 32232 schools, weather, environment and other info / rankings.




 8613869596835
8613869596835